38 aws security best practices
PDF AWS Security Best Practices Amazon Web Services AWS Security Best Practices Page 1 Introduction Information security is of paramount importance to Amazon Web Services (AWS) customers. Security is a core functional requirement that protects mission- critical information from accidental or deliberate theft, leakage, integrity compromise, and deletion. What is AWS Security? Risks, Best Practices, and More Here are some best practices to help you choose the right solution: Easy integration. Choose a security solution that integrates with AWS to make the process painless. Maintain visibility and control. To be able to effectively audit and control compliance, choose a solution that allows total visibility and control.
AWS Security Group: Best Practices & Instructions - CoreStack Here are six best practices to assist in that process. Avoid the use of the "default" security group The "default" security group should not be used for active resources. This is because new AWS resources could be inadvertently assigned to it and thus allowed inappropriate access to confidential material.

Aws security best practices
Top 10 security items to improve in your AWS account AWS recommends that you write logs, especially AWS CloudTrail, to an S3 bucket in an AWS account designated for logging (Log Archive). The permissions on the bucket should prevent deletion of the logs, and they should also be encrypted at rest. Once the logs are centralized, you can integrate with SIEM solutions or use AWS services to analyze them. 12 Important AWS Security Best Practices for 2022 To help customers secure their AWS environments, AWS has published twelve essential AWS Cloud Security best practices for 2022. These best practices cover various topics, including identity and access management, data security, incident response, and compliance. We've added a few best practices to the AWS list to help in identities, data ... AWS Security Best Practices | Global IT Training Currently, the average cost of a security breach can be upwards of $4 million. AWS Security Best Practices provides an overview of some of the industry best practices for using AWS security and control types. This course helps you understand your responsibilities while providing valuable guidelines for how to keep your workload safe and secure.
Aws security best practices. Best Practices for Organizational Units with AWS Organizations Jul 21, 2020 · AWS customers look to move quickly and securely when launching new business innovations. The multi-account environment provides guidance to help customers plan their AWS environment. This framework is designed to meet security needs, while maintaining the ability to scale and adapt their environments with changing business demands. The basis of a well-architected multi-account AWS environment Top 10 security best practices for securing backups in AWS If you leverage AWS Security Hub within your cloud environment, we recommend you enable the AWS Foundational Security Best Practices, as it includes detective controls that can help with securing backups in AWS. The detective controls in AWS Backup Audit Manager and Security Hub are also mostly available as AWS managed rules in AWS Config. Best Practices - Security - Amazon Elastic Container Service Each topic in this guide starts with a brief overview, followed by a list of recommendations and best practices that you can use to secure your Amazon ECS clusters. Topics Shared responsibility model AWS Identity and Access Management Using IAM roles with Amazon ECS tasks Network security Secrets management Security best practices in AWS IoT Core You can use AWS IoT Device Advisor to validate that your devices can reliably connect to AWS IoT Core and follow security best practices. IAM Policy Variables Amazon Cognito Identity AWS IoT Device Defender CloudWatch Logs for AWS IoT Keep your device's clock in sync It's important to have an accurate time on your device.
AWS Security Best Practices Checklist | CDW AWS security services can provide near limitless benefits to all aspects of your business or organization. Many of those services can be managed by a third party, saving you even more time, money, and hassle. While AWS security can be managed via a third party, some responsibilities must be addressed in-house. Following a set of AWS security best practices can help ensure that every aspect of ... 9 AWS Security Best Practices - Alert Logic [ Related: Data Security Best Practices] 6. Backup Your Data You never know if you're going to need to restore data after a breach, so back up your data regularly. You can do this by using AWS Backup. This app makes it easy to automate backups across your AWS environment, so you never have to worry about losing important information. AWS Top Security Practise | Top AWS Security Best Practices in 2022 Get free career guidance your next job AWS IAM Security Best Practices | Ankaa Pmo® While this blog post refers to AWS services, in particular, the best practices are mostly the same for any other IAM framework. "Security is job zero." When it comes to security in AWS, this is the de facto culture and standard. Source de l'article sur DZONE
AWS Security Best Practices - CoreStack Introduction - AWS Security Best Practices. AWS provides its users with a wide variety of managed security services, as well as security guidelines and patterns. When followed, these services help ensure that your business can meet any regulatory requirement. In fact, security forms one of the six pillars of the "AWS Well-Architected ... Best Practices | AWS Security Blog If you're looking to improve your cloud security, a good place to start is to follow the top 10 most important cloud security tips that Stephen Schmidt, Chief Information Security Officer for AWS, laid out at AWS re:Invent 2019. Below are the tips, expanded to help you take action. 1) Accurate account information When AWS […] Read More GitHub - prowler-cloud/prowler: Prowler is an Open Source ... Prowler is an Open Source security tool to perform AWS security best practices assessments, audits, incident response, continuous monitoring, hardening and forensics readiness. It contains more than 240 controls covering CIS, PCI-DSS, ISO27001, GDPR, HIPAA, FFIEC, SOC2, AWS FTR, ENS and custom security frameworks. amazon web services - AWS Security Groups best practices for RDS ... I have a lot of services which need to reach the RDS instance, what would be the best solution here : Create a SG rds_sg with an inbound/outbound rule allowing traffic on port 5432 (postgres) and self, assign this SG to the RDS and all services using the DB. Create a SG rds_sg_out allowing outbound traffic on port 5432 (on VPC cidr block) and ...
PDF AWS Security Best Practices - AWS Whitepaper Title: AWS Security Best Practices - AWS Whitepaper Author: Amazon Web Services Created Date: 20220613070632Z
ARCHIVED: AWS Tagging Best Practices Amazon Web Services – Tagging Best Practices Page 3 requirements. Tag stakeholders in an organization typically include IT Finance, Information Security, application owners, cloud automation teams, middleware and database administration teams, and process owners for functions such as patching, backup/restore,
PDF AWS Security Checklist For more best practices, see the Security Pillar of the Well-Architected Framework and Security Documentation. Notices Customers are responsible for making their own independent assessment of the information in this document. This document: (a) is for informational purposes only, (b) ... Amazon Web Services Created Date:
AWS VPC Security: 13 Best Practices [The 2022 Guide] The best practice is to split your production, staging, and pre-production environments across different VPCs. Image courtesy of AWS 5. Use Security Groups To Control Resource Access It's vital that you factor in AWS Identity Access Management (IAM) when you're planning and setting up your VPC.
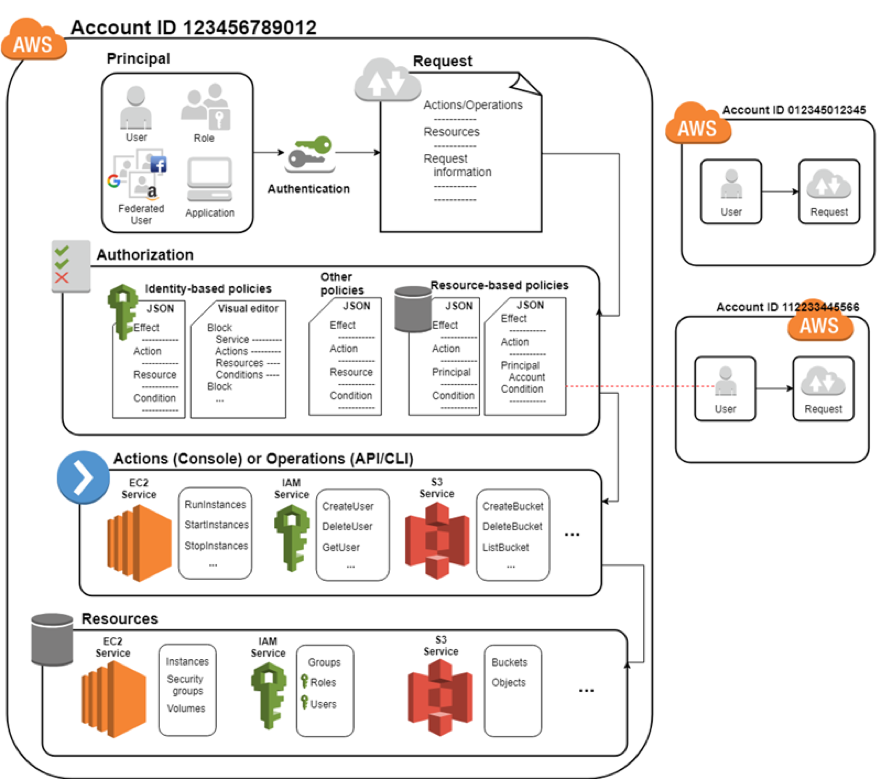
Security best practices in IAM - AWS Identity and Access ... AWS managed policies are designed to provide permissions for many common use cases. For more information about AWS managed policies that are designed for specific job functions, see AWS managed policies for job functions. Validate your policies. It is a best practice to validate the policies that you create.
AWS Security Best Practices Establishing best practices; Compliance in AWS; Module 2: Securing the Network. Flexible and secure; Security inside the Amazon Virtual Private Cloud (Amazon VPC) Security services; Third-party security solutions; Lab 1: Controlling the Network. Create a three-security zone network infrastructure.
Top 10 Best AWS Security Practices - Inverita 10 AWS Security Best Practices #1 Learn How to Use the AWS Well-Architected Framework. Half the work is done if you have a clear grasp of your security job and duties in the shared responsibility model. Then among the first topics, you need to learn if you're just getting started with AWS would be Well-Architected Framework. This will assist ...
Cloud Security – Amazon Web Services (AWS) With AWS, you control where your data is stored, who can access it, and what resources your organization is consuming at any given moment. Fine-grain identity and access controls combined with continuous monitoring for near real-time security information ensures that the right resources have the right access at all times, wherever your information is stored.
AWS IAM Security Best Practices. Identity and access management is a ... For most apps that need access to AWS, the best practice is to configure the program to retrieve temporarysecurity credentials using an IAM role. With that in mind, do not put access keys within...
Security, Identity & Compliance | AWS Architecture Center Best Practices for Security, Identity, & Compliance Learn how to meet your security and compliance goals using AWS infrastructure and services. To learn current AWS recommendations and strategies to use when designing cloud architectures with security in mind, see the Security Pillar - AWS Well-Architected Framework.
How to secure an enterprise scale ACM Private CA hierarchy for ... In this post, we show how you can use the AWS Certificate Manager Private Certificate Authority (ACM Private CA) to help follow security best practices when you build a CA hierarchy. This blog post walks through certificate authority (CA) lifecycle management topics, including an architecture overview, centralized security, separation of duties, certificate issuance auditing, and […]
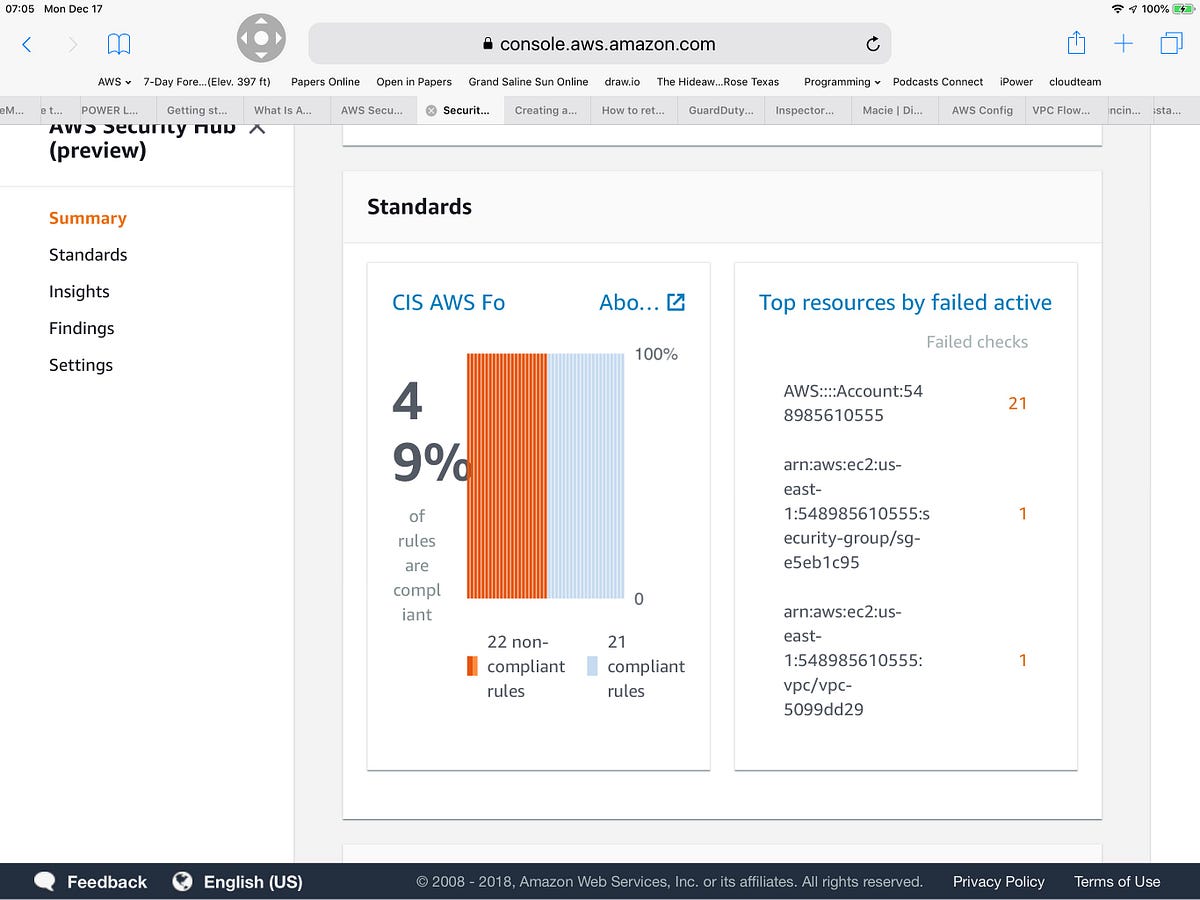
AWS Foundational Security Best Practices standard The AWS Foundational Security Best Practices standard is a set of controls that detect when your deployed accounts and resources deviate from security best practices. The standard allows you to continuously evaluate all of your AWS accounts and workloads to quickly identify areas of deviation from best practices.
Home - EKS Best Practices Guides - GitHub Pages This guide provides advice about protecting information, systems, and assets that are reliant on EKS while delivering business value through risk assessments and mitigation strategies. The guidance herein is part of a series of best practices guides that AWS is publishing to help customers implement EKS in accordance with best practices.
13 AWS Security Best Practices - Check Point Software By following this AWS security best practices checklist, it is possible to improve the security of an AWS deployment. Identify Security Requirements 1. Define and Categorize Assets in AWS: It is impossible to secure systems that you don't know exist.
AWS Security Best Practices Notice: This whitepaper has been archived. For the latest technical information on Security and Compliance, see ...
Nine AWS Security Hub best practices | AWS Security Blog In this post, I'll provide nine best practices to help you use AWS Security Hub as effectively as possible. 1. Use the AWS Labs script to turn on Security Hub in all your AWS accounts in all regions and to establish your existing Amazon GuardDuty master/member hierarchy
AWS Security Best Practices | Global IT Training Currently, the average cost of a security breach can be upwards of $4 million. AWS Security Best Practices provides an overview of some of the industry best practices for using AWS security and control types. This course helps you understand your responsibilities while providing valuable guidelines for how to keep your workload safe and secure.











0 Response to "38 aws security best practices"
Post a Comment